WireGuard for GL-iNet routers
Connecting sites can be both easy and hard, depending on what’s your skillset, what gear you have and most likely: what’s your personal preference for achieving your targets. If you ask professionals how to connect two sites (e.g. your home lab with a remote backup location), you’ll most likely get the answer to simply connect two routers via IPSEC or OpenVPN and you’re done.
Yeah, sure. That’s how we’re doing it for years, using a pretty solid and more-or-less easy to configure site-to-site VPN solution which is both used in SOHO and medium to large enterprise environments. The new kid on the block is WireGuard, which got a lot of noise and attraction the last years, because of the following reasons:
- better architecture and design: you don’t rely on stuff like handshake authentication and other “heavy” mechanism
- security: you basically don’t sacrifice speed for security because of newer cryptography like ChaCha20 (instead of AES-256)
- speed: WireGuard runs on kernel level instead of the userspace
- simplicity: less code, less troubles, leading to better user experience
So how to get along with it? Recently I needed to setup a site-to-site connection for an external contractor, a so-called one-person-company, which is travelling a lot, often works from hotel rooms and doesn’t want to invest hundrets of dollars in a small enterprise router or firewall, just to connect to his remote storage location via WireGuard. Off course he could simply use the WireGuard client on his MacBook, but for specific reasons he needed to provide VPN network access to a few other clients on-site, both connected wired and wireless, which cannot simply use the WireGuard client. So he itself came with GL-iNet - a company that produces small, lightweight, OpenWRT-based routers, access points and IoT gateways. Nice company, didn’t know it before!
Don’t get me wrong: GL-iNet is one vendor of many. There’s absolute no preference on that side, everything could be also done with enterprise vendors, Ubiquiti stuff, TP-Link or any other Linux- or OpenWRT-based gear. I said: “great, let’s give it a try, the price-performance ratio seems to be good”.
The admin panel is nice, you can use features like wireless repeater, tethering, OpenVPN or WireGuard server/client, Tor or AdGuard, and even install additional OpenWRT-packages.
Where it gets interesting is the WireGuard client feature. This seems to work great out-of-the-box if you’re using a typical VPN provider like Mullvad.
After having a “deeper” look into the feature, I realized: yeah, cool, but unuseable. Let’s stick to native OpenWRT 😉
Fortunately, you can browse to http://<router-ip>/cgi-bin/ and configure everything in OpenWRT.
I will not go into how to configure a WireGuard server, this off course depends on the technology. We’ll now focus on how to setup the WireGuard client in OpenWRT.
- Install the necessary packages:
qrencode luci-proto-wireguard - Add a new WireGuard interface in
Network -> Interfaces - Edit the interface:
inGeneral Settings, generate a new key and save it somewhere
inFirewall Settings, assign the LAN zone (depends on your setup) together with the WG zone
inPeers, enter your WireGuard server public key and settings (endpoint host and port), set the remote subnet(s) inAllowed IPsand generate a QR code to get all client infos (incl. peer public key) - Save the config
- In your WireGuard server, now add/allow the peers public key
You now should see a tunnel connection getting established. If not, try to access (ping, http, whatever) a remote ressource - by default, the WireGuard client only establishes a tunnel when there’s a reason to do so.
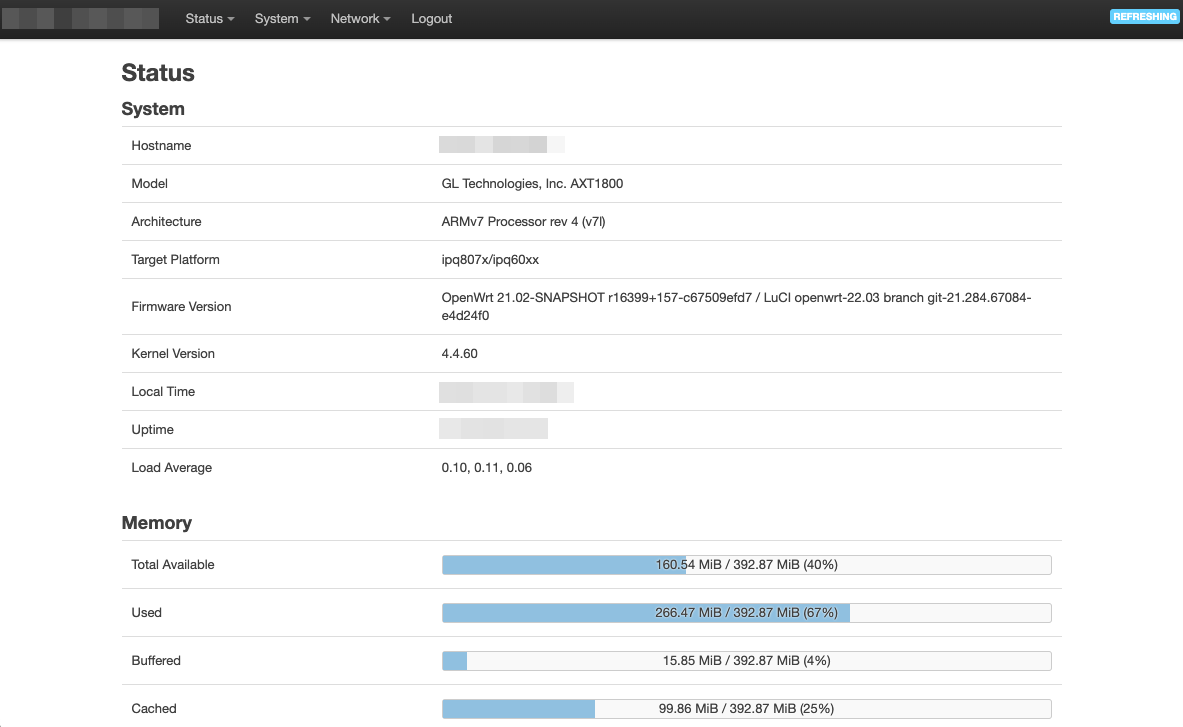
In my setup, I now have a up-and-running WireGuard tunnel, both from the client side…
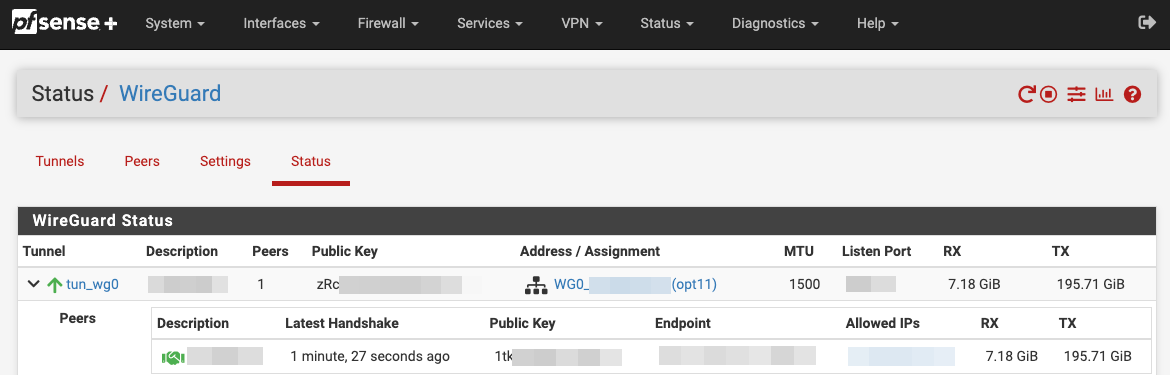
… and from the server side (in my case, a pfSense firewall)
If you need a more detailled guide on how to setup WireGuard on pfSense, just let me know!